By Xander Snyder
In a world where technology is such a critical element of a country’s functioning and security, a national defense strategy has to be able to address more than just military threats. Cyberattacks that target computer networks and systems can cripple a country’s ability to wage war and defend itself against an attack.
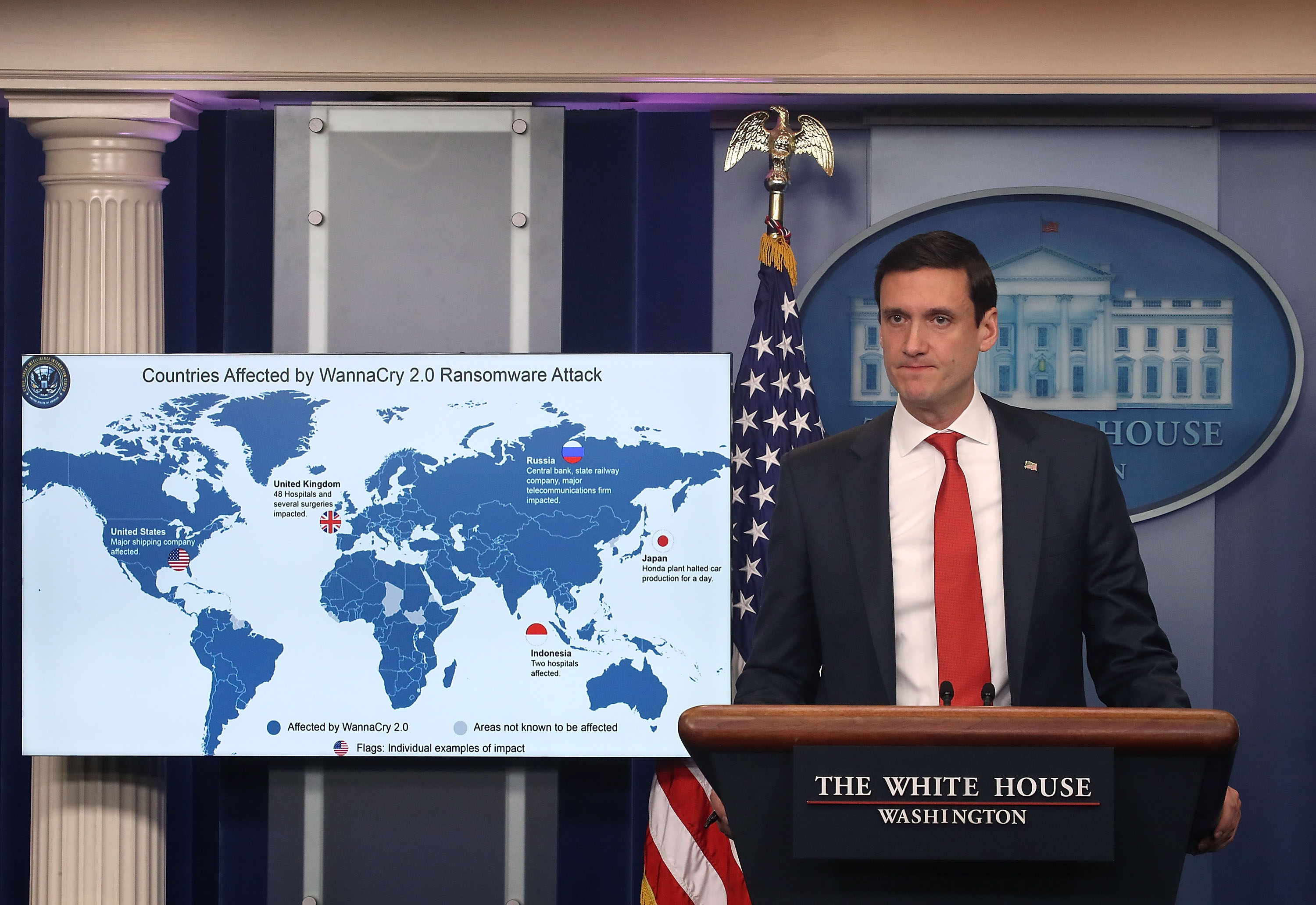
Earlier this year, the WannaCry cyberattack, which affected hundreds of thousands of people as well as major infrastructure, proved that such attacks can have global implications. On Dec. 18, White House homeland security adviser Tom Bossert announced that the U.S. has determined that North Korea was responsible for the attack.
The virus froze computer systems, requiring users to pay a ransom in bitcoins to have their computers unlocked. Bitcoin accounts are anonymous, but all transactions are stored on a ledger and publicly available, so the amount of money raised in the attack can be determined with accuracy. Though there is some skepticism in the cybersecurity world as to whether the attackers were able to draw down the bitcoins, they did raise $143,000, which is equivalent to about $1.2 million now because of the recent dramatic rise in the price of bitcoin.

Tom Bossert, White House homeland security adviser, briefs reporters about the WannaCry cyberattack earlier this year at the White House on Dec. 19, 2017. Mark Wilson/Getty Images
This isn’t the only bitcoin-related cyberattack that North Korea has been implicated in. In April, it allegedly attacked a South Korean bitcoin exchange called Youbit, stealing $5 million worth of bitcoins. On Dec. 19, Youbit announced it had been subject to yet another attack – North Korea is also suspected to be involved in that one – and has had to declare bankruptcy as a result. In July, North Korea is believed to have attacked another cryptocurrency exchange, collecting the equivalent of $7 million.
Why does North Korea want bitcoins? The country faces severe sanctions that isolate it from the international financial system, and bitcoins provide the regime with a way to more easily move money across borders and get around the sanctions. This enables North Korea to bring funds into the country and transfer payments outside of the country – which is useful when it needs to pay entities for carrying out illicit activities like cyberattacks. It’s believed that the WannaCry attack was executed through a hacker group called Lazarus. The group may be located outside of North Korea, so Pyongyang needs to ensure that it can pay its cyber mercenaries to maintain this capability.
It’s unclear whether this group operates independently and was simply commissioned by Pyongyang, or whether North Korea provided it with technological expertise. Either way, the extra layer of separation provides a degree of anonymity – albeit limited anonymity, since U.S. authorities and independent security experts have been able to identify those responsible – and plausible deniability for North Korea.
Demonstrating Capability
If North Korea is in fact responsible for WannaCry, it would be consistent with the way Pyongyang has used its missile tests to demonstrate its capabilities without doing enough damage to seriously risk a U.S. retaliation.
The WannaCry attack affected the United Kingdom’s National Health Service and some critical U.S. infrastructure. In June, a similar cyberattack also hit Ukraine’s state power provider. None of these attacks, however, caused serious damage.
This brings us back to the U.S. announcement about North Korea being responsible for the attack. Though there is some skepticism in the cybersecurity community, most experts agree that Pyongyang was behind it. But why would the U.S. make this announcement now? The U.K. National Cyber Security Center announced in October that it had known since July that North Korea was behind the attack. The two countries are close allies, and the U.K. would have shared this information with the U.S. There’s no reason to think that the U.S. was unaware of the intelligence that led the U.K. to make this conclusion.
The answer may come from the new U.S. national security doctrine, released earlier this week. It states that nuclear weapons play a role in deterring not just nuclear attacks but also other types of attacks: “While nuclear deterrence strategies cannot prevent all conflict, they are essential to prevent nuclear attacks, non-nuclear strategic attacks, and large-scale conventional aggression.”
The document does not define non-nuclear strategic attacks. But as The Guardian’s world affairs editor pointed out, the U.S. deputy assistant secretary of defense for nuclear missile policy, Rob Soofer, provided a definition in September. His definition included “cyber-attacks against U.S. infrastructure.” If we apply this definition to the new U.S. security doctrine, the U.S. seems to be implying that it can use nuclear weapons to respond to cyberattacks.
A Proportionate Response?
A nuclear response in this case would raise a question about proportionality: To successfully apply a deterrence strategy, a country’s response, once attacked, should be proportionate to the scale of the initial attack. This makes it clear to all adversaries that the country is willing to follow through on its threats. Scale can be measured by the number of casualties or the extent of infrastructure damage. Until now, massive damage to strategic infrastructure has been incurred only through the use of military weapons. A nuclear response to the WannaCry attack would be an example of an asymmetric response. But if WannaCry was, like Pyongyang’s missile tests, a way to demonstrate capability without actually crossing a line – which seems like a reasonable interpretation since the damage was not severe – then it could be reasonably assumed that Pyongyang does possess the ability to do greater damage to U.S. infrastructure than it did.
By releasing a new policy that justifies nuclear retaliation against non-nuclear strategic attacks and then identifying North Korea as the culprit in the WannaCry attack, the U.S. is making the case that, if it launches a nuclear strike, it shouldn’t necessarily be considered a first strike but a retaliation against North Korea’s cyberattack.
This does not mean that the U.S. is gearing up to use nuclear weapons in response to the WannaCry attack. But the U.S. is trying to recalibrate North Korea’s calculations. It is sending a message to Pyongyang that a cyberattack can lead to a substantial non-cyber response. It is also making the argument that it would not be carrying out a nuclear first strike if it were to respond to a North Korean cyberattack with nuclear force, thereby avoiding setting precedence for a nuclear first strike. Regardless of whether North Korea takes the U.S. at its word, introducing the threat of nuclear retaliation to a non-nuclear attack substantially increases the risk involved in carrying out these cyberattacks.






 Special Collection – The Middle East
Special Collection – The Middle East