By George Friedman
Last Friday, major websites in the United States were shut down in denial-of-service attacks. These attacks are essentially carried out by overwhelming a system with excessive requests and making it inaccessible to users, thereby shutting it down. What made this attack different than the many others launched was its size. These attacks are most effective when other servers and devices are used, without the owner’s knowledge, to overload the site being attacked. In this attack, not only conventional computing systems were used, but the vast array of devices that are increasingly accessing the internet and operated using mobile devices. For example, a coffeepot that can be connected to the internet so you can order it to start brewing from bed. This “Internet of Things” was essentially hijacked to carry out the attack.
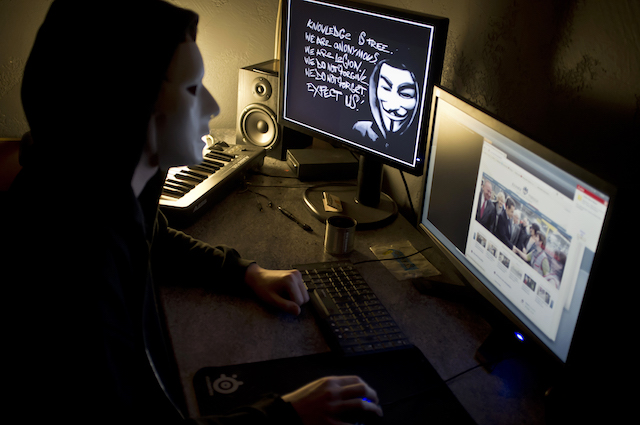
A masked hacker, part of the Anonymous group, hacks the French presidential Elysee Palace website on Jan. 20, 2012 near the eastern city of Lyon. Anonymous, which briefly knocked the FBI and Justice Department websites offline in retaliation for the U.S. shutdown of file-sharing site Megaupload, is a shadowy group of international hackers with no central hierarchy. JEAN-PHILIPPE KSIAZEK/AFP/Getty Images
At a certain level, this is no different from the hacking epidemic that has affected not only the presidential campaign, but other public figures. To send and receive emails, you must be online, and if you are online you are vulnerable to the intrusion of outside programs that can extract information from your computer. Just as you cannot tell if your coffeepot has been turned into a bot, you cannot know if – or who – has accessed your email. I have had my own experience with this and can attest to the difficulty of knowing who has taken control of the system, and the even greater dilemma of not knowing whether the person who is supposed to know these things actually does.
Friday’s attacks and the recent email hacks were not by themselves all that significant. For some, Twitter withdrawal might be painful, but on the whole what is noteworthy about the attacks is that they were intended to be intrusive and annoying without causing any serious problems, as if they were a warning. Hospitals, aircraft and other essential services were not the target. It leaves us to wonder who was behind this, but that can’t be known. And that is the point – you can point your finger at the Russians or bright 16 year olds, but it is clear that one of the things the internet promised – anonymity – has been fulfilled.
We need to remember why the internet was invented in the first place. The Defense Advanced Research Projects Agency was looking for a more efficient mechanism for moving files between the national labs doing defense work. It was a means of moving data, because copying and FedExing papers took too long. At the same time, the personal computer was maturing. Its operating system envisioned a standalone system, not connected to a network, that could carry out a range of computing functions.
Without intention, an operating system designed for a standalone system was married with a modem that could connect the computer to the internet and became a jury rigged communications system that could move data and files from point to point. I remember being a professor in 1985 and requiring students to submit papers by computer, for no particular reason other than I could and thought it was cool.
The point is this. There was no architect of the internet. No one ever foresaw how it would develop. And no one ever envisioned it as a mission critical device, which would cause catastrophe if it failed and was in a position to stop and reinvent its components. The internet just unfolded. The government got involved in coming up with a site naming convention, and someone determined that the useless character @ would from then on mean “at.” But aside from such peripheral issues, no one ever set limits. And without limits it has become, in a generation, the foundation of modern life.
Its weakest link is not in communications but in the operating system that runs all devices. Apart from some fundamental systems programs, the operating systems are software. Where hardware tends to be static, software is by definition dynamic. In the course of operation, it shifts its shape constantly. It is efficient to install, inexpensive to reproduce, quick to update and plays well with other software. Hardware is built to accommodate this dynamism. The underlying infrastructure is itself software and built with the same characteristics as other software with one additional element. Modern software evolved out of prior and very old operating systems. It is to some extent an archaeological dig in which old, vestigial code still lives, apparently without much purpose, except for issuing random and meaningless commands.
Now, data is also flowing into your computer every time you visit a website. Your computer’s code is constantly in action. There is no overall system that is charged with knowing what is there, what is not supposed to be there and so on. Virus scanners look for the intrusion of known malware, but can only identify certain malware. And those who are planting the malware know the limits of your scanner.
This means that a 16-year-old kid may well figure out a set of code that can attack your computer without giving any indication of its presence even when executed and that does something to your system or installs itself on other systems. You will not know that the code exists, who sent it or where it is going.
We speak about artificial intelligence, by which we mean machines that have some degree of self-awareness. I don’t know that I would call this intelligence, but I would regard it as the foundation of the internet’s next form. We need an operating system that knows what is supposed to be on our computers, that knows what it may and may not do, and that does not admit any piece of software without bearing the electronic signature of its sender, validated against a master list. In other words, when someone enters your email, the system knows it, knows who did it and notifies you.
I do not know how to build this, nor do I believe even this system would be foolproof. The best you can do to protect yourself is to fortify your electronic devices and have the ability to trap the attacker. It cannot be perfectly done. But right now, we are not even trying. Our defenses primarily target penetration by known attackers. But significant damage can be done by unknown attackers.
This proposal will also reduce the anonymity of the internet. I am not sure that would be a tragedy. Knowing who is trying to exploit children is a good idea. And if shame has any force today, some of the more lunatic threats on the internet might subside. But this is not the key to this problem. The key is geopolitical. According to the U.S. government, the Russians have attacked the Democratic National Committee servers. Russia denies it. The U.S. responds. This situation can escalate.
The “Model T” internet developed without any real planning. I watched it grow, having no idea what it would become. It now contains our weapons, our hopes and our secrets. It wasn’t meant to, but this has become a major vulnerability. Wars have been started over and with less.






 Special Collection – The Middle East
Special Collection – The Middle East